The Most Trusted Cyber Security Companies- 2025

In the interconnected world we live in today, trust has become the cornerstone of every successful business relationship, particularly in the digital realm. As industries continue to embrace digital transformation, cybersecurity has shifted from being a specialized IT function to becoming a critical business imperative. Cyber threats grow more sophisticated by the day, and the responsibility of safeguarding data, operations, and trust rests heavily on the shoulders of cybersecurity companies.
Redefining Innovation and Empowering Global Enterprises with Automated, Secure, and Sustainable Cloud Solutions

In today’s world, technology is the game-changer that is reshaping lives, powering sustainability, and advancing society in unimaginable ways. Yet, as fast-paced as the tech world moves, it’s easy to lose sight of original visions, and some lose momentum or veer off track long before they can pivot back. Amid this whirlwind, Pvotal Technologies stands out by staying laser-focused on the ultimate goal—transforming the complexity of innovation into practical solutions that businesses and individuals can truly benefit from. Pvotal Technologies has redefined tech development through cutting-edge automation and best practices across AIOps, BizDevOps, DevSecOps, CloudOps, and ITOps. Their low-code, event-driven, microservices-based Cloud Native platform enables businesses to launch products in half the time and at a fraction of the cost of traditional methods. What sets Pvotal apart is its visionary approach to innovation. The team embraces challenges as opportunities, fostering a culture of collaboration and specialization. Rather than competing, they set high standards for speed, accuracy, and security, striving to build “Infinite Enterprises”—organizations designed for rapid change and scalability. At CIO Bulletin, we had the honor of interviewing Elisabeth Beiter, CIO of Pvotal Technologies. In our conversation, she shared valuable insights into how she and her expert team are dedicated to transforming clients’ digital journeys and achieving seamless cloud excellence in a rapidly evolving technological landscape. Interview Highlights Can you share the story of how Pvotal Technologies was founded and what inspired its creation? Pvotal began its journey in June 2021, aiming to transform manual processes and pain points in the equine industry through technology. As we addressed technical challenges, we recognized that relying on numerous third-party vendors for an enterprise-grade solution could lead to significant issues, including data breaches, rising operational costs, and recurring vulnerabilities. To tackle this, we developed our proprietary Cloud Native platform, allowing rapid progression from concept to secure, scalable deployment without major third-party services. We utilized tools from leading open-source projects, evolving them into our platform engineering solution: Infrastream. Our goal is to empower every enterprise to become self-sufficient and build applications comparable to those of Google, Netflix, or Uber, while reducing costs and workforce needs. Today, we’re passionate about applying these methodologies across industries, enabling clients to achieve transformative outcomes. Our Principles More automation: We believe in making viable products that withstand the test of time, so we’ve chosen to develop a high level of automation to produce hyper-scalable technologies.Fewer tools: We use a lean number of third-party tools, leveraging a stringent third-party selection process to ensure a similar level of security commitment to protecting client data and appropriate turnaround time for security fixes. More optimization: We fully optimize our tools using custom scripts, modules, and proprietary methodologies, particularly regarding service accounts and networking. Fewer attack surfaces: By restricting the number of tools, we expose fewer attack surfaces. More security: With fewer attack surfaces and more automation, we lower our risk for error with each deployment. Our cutting-edge Cloud Identity and Infrastructure ensure that user data is always secure and that each transaction is protected. What are the core products and services that Pvotal Technologies offers, and how do they address the unique needs of your clients? In the ever-evolving digital landscape, internal developer platforms are increasingly common, primarily focused on simplifying builds and deployments. However, Pvotal is redefining cloud infrastructure management with a GCP-first strategy. Our platform, Infrastream, will be easily deployable directly from the Infrastream website and, in the future, will also be available via the GCP Marketplace, allowing organizations to standardize infrastructure management. This enables Pvotal to deliver integrated, cloud-native management tailored for Google Cloud Platform (GCP). As an infrastructure-as-code solution, our platform uses opinionated configuration manifests to orchestrate every aspect of a managed Google Cloud organization, ensuring seamless delivery from the source code repository to container deployment. By embracing this innovative approach, Pvotal eliminates reliance on error-prone infrastructure scripts, providing a robust, actionable baseline that delivers immediate value with minimal consulting. Our solution also supports long-term maintenance of project deployment engines such as GCE, GKE, and Cloud Run. What sets Pvotal apart is our holistic vision: Comprehensive Automation: We automate the management of the entire cloud environment, addressing technical requirements across all business lines and ensuring functionality despite knowledge gaps. Security by Design: Our platform integrates security from the ground up, minimizing risks and ensuring compliance without added costs, safeguarding your organization’s data and resources. Actionable Insights: We provide intuitive visualizations within a centralized portal, empowering teams to make informed decisions and manage deployment timing effectively. Managed Secrets and Configurations: Our platform simplifies handling sensitive data and complex configurations, significantly reducing potential human error. At Pvotal, we empower companies to achieve greater agility, security, and efficiency through simplified infrastructure-as-code manifests, transforming how businesses engage with their cloud infrastructure. Additionally, we support organizations without in-house engineering teams through our end-to-end consulting and venture-building offerings, comprehensively addressing all their technical needs. Pvotal Technologies has made remote work the norm. Can you share specific strategies or technologies that have made this transformation possible and how this has impacted productivity and employee satisfaction? Our decision to embrace remote work is a direct reflection of our core philosophy: the strength of an organization lies in the quality of its people. By opening our minds and policies to talent from around the world, we attract incredibly skilled individuals who bring diverse perspectives and innovative solutions to complex problems. This approach is evident in the unique technologies we have built and the exceptional client experiences we provide. Operationalizing an effective remote working model has been integral to our success. We follow several practices to ensure visibility, share cross-team strategies, build complementary teams, and provide our high achievers with exceptional opportunities. At Pvotal, we’re not just a team of remote workers; we’re a family of digital nomads, united by our shared passion for innovation and excellence. We work hard, we play hard, and we always celebrate our successes together. How do your in-house UI/UX designers balance keeping up with the latest design trends while ensuring accessibility in the products they create? The culture of our design team
AITech Interview with Yashin Manraj

Yashin Manraj, CEO of Pvotal, redefines enterprise scalability and security by eliminating tech debt and building resilient systems for future innovation. Yashin, to kick things off, could you share what inspired you to transition from a career in academia and engineering to founding Pvotal Technologies? Growing up, I thought a lack of proper education was the root of many societal issues and inefficiencies. Idealistically, I entered academia thinking I could become a professor who would nurture the issues leading to a wavering generation of talent, innovation, and development. Unfortunately, I quickly realized how some processes were limiting, stifling, and stuck in an antiquated age. I could not build or address problems I saw in my niche field due to software issues, data breaches, the high cost of licensing fees for some critical tools, and the poor integration of tools. These issues led me to lose thousands of hours in frustration fixing technical problems rather than focusing on my growth, thesis, and research. The tools I used became a greater source of frustration than my research, constantly distracting me from my objectives. My skills and resolve were too limited to reform academia from within, so I decided to focus on the issues within the software industry to limit the problems that more talented academics faced. I co-founded Pvotal with Ashley to build a new generation of solutions that helped customers focus on the value they bring to customers rather than get stuck in an iterative cycle of integrating code and debugging updates. Pvotal emphasizes creating “Infinite Enterprises.” Could you explain what this concept entails and how it aligns with your overall mission? While many industries have adopted different interpretations of the ideal Infinite Enterprise, we believe the “infinite enterprise” is any company that has achieved an infinitely scalable, independent, resilient, and secure infrastructure. Once these criteria are met, we observed that it allows businesses to truly innovate, improve, and elevate their value proposition to customers. The age-old adage of teens or some fresh graduates going into “founder mode” can build the next generation of software in their proverbial garage, shared workspace, or dorm room is simply no longer possible. The rise of hyperspecialization, wanton integration of third-party code or vendors, and the unmanaged accumulation of technical debt has led most software companies to become antiquated, vulnerable, and overbloated pieces of code that can no longer efficiently protect their customers’ data, provide a competitive edge to their users, and have a reasonable cost/utilization footprint. Most modern enterprise software has at least 17 paid or free SaaS, PaaS, and third-party code powering its operation or development. With a tough economy, inflation, and squeezed supply chains, these different services are forced to raise prices continually, thus shifting the burden on the end consumer. In addition to the increasing costs, these software are often abandoned or introduce vulnerabilities to the enterprise supply chains, which is why we have experienced a record-breaking number of successful cyberattacks, ransomware, and fraud every year for the past decade. Our version of the Infinite Enterprise is to break the vicious cycle we have been forced into and empower businesses to move forward unhindered by these financial, technical, and logistical barriers placed by the status quo. Threat intelligence is a critical aspect of cybersecurity. How does Pvotal approach proactively identifying and assessing potential threats in today’s rapidly evolving landscape ? We started by recognizing that we cannot be reactive to threat actors and trying to defend against each type of potential threat. It is futile to try to anticipate how nation-state actors like Russia, Iran, and North Korea will act or how private groups may attack our systems. We developed a proactive methodology similar to that of Google, Netflix, or Uber. In our version of Zero Trust Methodology, we created our own privilege engine and network isolation protocols. We are able to minimize the potential attack surface and shift key processes and infrastructure to be accessible only to core automated services. We use secure runtimes like restricted Golang and Rust binaries within containerized images and automate our deployment to eliminate human intervention and the potential for human error. Our core services have no third-party code, service, or API, giving us unparalleled flexibility to iterate, ideate, and price our services competitively. By significantly reducing the potential surface attack vectors, we can skip on expensive, tedious, low-performing identification or assessment libraries that often fail to yield significant results in shielding businesses from the rapidly evolving threat landscape: we limit the potential for initial exposure and post-exploitation phases. Our skeptical approach of “never trust, always verify” allows us to successfully enhance our security posture and minimize the risk of lateral movement in the unlikely event of a significant breach. We further decouple infrastructure components through Infrastructure as Code (IaC) to enable rapid patching cycles, automated library updates, and reduced human activity within fast deployment cycles. We can push thousands of daily updates without downtime or impacting our clients, services, or usability. Your company advocates for a comprehensive security stack. Can you discuss the key components of this strategy and why a layered defense is essential ? A layered approach is the only practical approach to providing redundancy and resilience. It ensures that if one layer is compromised, others remain in place to prevent a full-blown security breach. However, our underlying strength lies in how each layer is selected, engineered, and structured. Each layer adopts the best industry practices from mature cloud-native open-source projects; no third-party code or licensed product is included, and code is constantly refactored to reflect changing attack methodologies and zero-day vulnerabilities. We have a dedicated team that engineered the layers and maintained their operational excellence by continuously monitoring threats and vulnerabilities exploited globally. This helps us maintain a lean and tightly controlled ecosystem with a manageable number of operational runtimes that power even the most complex use cases: we attempt to maintain less than 5% of legacy code and no shadow IT/API. We extend our infrastructure level defenses to applicative
New Email Scam: The Alarming Way Your Money Could Disappear

A new form of email scam uses photos of your home to deceive victims into sending money or Bitcoin. You receive an email from an unknown sender, which includes a picture of your home and address, accompanied by a threatening statement: “Don’t make the mistake of hiding. You have no idea what I’m capable of… I have recorded videos of you doing embarrassing things in your home (nice decor, by the way).” While it sounds like a horror movie plot, it is actually one of the latest phishing scam techniques. How the Email Scam Works Like many other email and SMS scams, this specific extortion scam uses personal information to trick people into sending money. The email convinces people that the hacker knows more about them and that they must make a payment or send Bitcoin to keep their information safe. “I received a PDF via email that included my address and a photo of my home, making improbable claims about my personal behavior and claiming to have recorded video documentation captured by spyware on my computer,” said Jamie Beckland, Director of Products at APIContext, to HuffPost. “The scammer threatened to release the video unless I paid them in Bitcoin.” If you receive a similar email, here are the steps you can take to identify if it is a scam and protect yourself: Many phishing scams are often filled with grammatical errors and poor formatting, making them easier to spot. However, this scam, involving home images, is a new, darker development. How Did the Scammer Find Your Home Address? According to Al Iverson, a cybersecurity expert and head of research and community engagement at Valimail, the sender likely obtained your address from a previous data breach that leaked personal details and then used a photo from Google Maps to compose the email. Beckland was able to confirm it was a scam by comparing the image in the PDF with the image of his home on Google Maps. Most images in these scams come from online sources, so he suggests people check if the image has been copied from the internet. If it has, it’s clearly not legitimate. Iverson recommended verifying the legitimacy of the email address whenever you receive correspondence from unknown users. “Check if the sender’s domain matches the official website of the organization,” he suggested as an example. "Also, if you use Gmail, look for the ‘Show Original Message’ option and examine the SPF, DKIM, and DMARC results.” These are essentially methods that verify the sender’s domain to prevent spam, phishing attacks, and other email security risks. “All of these should ideally pass the authentication checks,” added Iverson. “In other words, it should say ‘PASS’ next to all three options.” If an email looks legitimate, you might mistakenly click the links it contains for more information. Zarik Megerdichian, founder of Loop8, a company that protects personal data and privacy from data breaches and hackers, strongly warns against this. “Ensure that every time you’re asked to click a link in an email,” said Megerdichian. “Bitcoin transactions are irreversible, as are many other common payment methods, including Cash App and Zelle.” Update and Change Your Passwords It is also crucial, when faced with an extensive scam, to change all your passwords. “Use a new email address if possible and move critical financial or services to it, then begin reporting the case to local police, the FBI, and ensure your family is aware of the potential threat of public embarrassment in case they managed to steal any incriminating data,” said Yashin Manraj, CEO of Pvotal Technologies, a company that creates secure technology infrastructures for businesses. Don’t Engage with the Scammer It might be tempting to respond to an email (especially those that seem very realistic) to negotiate with the scammer. However, Manraj suggests withdrawing and ignoring these emails, as responding can actually put you on call lists and target databases, making you vulnerable to further attacks. Be Careful with Your Data in the Future Users must remember that data is a commodity, and businesses today collect far more information (often more than they need to complete the transaction). When signing up for new websites or downloading apps, Megerdichian suggests avoiding over-sharing information. “Always ask yourself, do they really need to know this? It is the consumers’ responsibility to be proactive about their personal data,” said Megerdichian.
If You Get a USPS Scam Text, You Need To Do This Immediately
Just yesterday, and last week, and the week before that, I got text messages from USPS informing me I had a package that couldn’t be delivered due to an incomplete address. To fix it, all I needed to do was click on a link and enter my personal info… Nope, I’m not falling for that scam text! And I’m not alone. More than 400 million scam texts arrive on phones across the country every day, with an uptick during shopping events like Prime Day and Cyber Monday. “Since the pandemic, online shopping has skyrocketed, and scammers tend to follow where the crowd goes,” says Vinicius Perallis, CEO of Hacker Rangers. “The more people shop online, the more these criminals take advantage of that behavior by sending out scam texts, pretending to be companies like USPS.” If you’ve received a text from USPS, UPS or another shipping company, here’s how to recognize if it’s a scam and what to do next. What Is Smishing? Smishing, or SMS phishing, is a type of fraud that attempts to use text messages to trick people into giving away sensitive information, clicking on a link that loads malware onto their device, or taking them to a deceptive website. And it’s surprisingly effective: according to research by Bitdefender, about 15% of people who receive these SMS messages end up clicking on a link. “Although phishing has been a known technique for a long time, [it’s] still extremely successful because consumers and businesses are still struggling to effectively defend against them,” says Ben Eichorst, Director of Infrastructure Security at Yubico. What To Do If You Get USPS or UPS Scam Texts First, if you get a message you think is a scam, don’t click on the link, and also refrain from replying. “These texts are annoying, and it’s tempting to reply with a few choice words,” says Seth Geftic, Vice President of Product Marketing at Huntress. “But you’re letting the scammers know your phone number is active, meaning you could receive more scam texts in the future.” Instead, block the number on your device and report the text to the FTC by forwarding it to (7726) SPAM. For USPS, also send it to spam@uspis.gov. “This not only helps protect others but also gives USPS important information to fight these scams,” says Perallis. Next, delete the text so you don’t accidentally hit the link later, which could be loaded with malware. As an added precaution, watch your bank accounts for unusual activity. If you’re unsure whether a text is a scam, ask the organization by using contacts on their official website. Verify tracking numbers directly on the USPS or UPS website. If they’re invalid, they’re probably a scam, says Perallis. Also, find updates for ongoing scams and suggestions for what to do directly from USPS and UPS. What To Do If You Engaged With a USPS or UPS Scam Text? If you clicked on a link from a scam text and entered login information, like for your USPS account, change your password immediately both on that site and for any other sites on which you’re using that password, says Perallis. Then: If you gave out financial details, like a credit card number, call your bank to report it and watch statements for suspicious charges. If you provided personal information, like your Social Security number or address, monitor your accounts for signs of identity theft. If you clicked on a link and now think it might’ve been a scam, run a virus scan on your device for malware. What Do USPS Scam Texts and Others Look Like? Scam texts are ever-evolving and can take a number of forms, but in general, look for: Grammatical mistakes, strange punctuation and misspellings. “There is a theory that scammers do this deliberately, as people who reply to these messages might be more vulnerable to scams than your average person,” says Geftic. A sense of urgency, with alarming or threatening language aimed at getting you to take action without thinking. A request for personal or financial information, including passwords, credit card numbers or your date of birth. “A legitimate courier mall company does not and will not, out of the blue, send a text message requesting for more details or money,” says Chris Dukich, CEO of Display Now. A link to a website that includes misspellings, strange numbers or abbreviations. Also, if you’re not expecting a package, that’s a red flag, since USPS doesn’t send texts unless you’ve requested tracking updates, says Yashin Manraj, CEO of Pvotal Technologies. “We recommend considering all text from unknowns as scams or spam and slowly building up a contact list of trusted providers,” he says. “For example, UPS will use 4601, 5289, 48515 or 69877, while USPS uses 28777.” What Does It Mean If You’re Getting Smishing Texts? There are many reasons you might be getting scam texts, from your number being involved in a data breach to entering your info on an unprotected website to your number coming up on automated random number-generating software. It doesn’t mean the scammers targeting you specifically, says Dukich. “Scammers usually send enormous amounts of messages and hope for the best,” he says. How To Protect Yourself from Scam Texts Besides not opening any links and not responding, in general, never share personal information, like your banking password or credit card information. It is unlikely any legitimate organization would ask for this via text. Also: Use spam blockers provided by your network provider. Don’t freely give out your mobile number online. Manraj suggests using a virtual number in all online stores, which you can get from most modern app stores. Regularly update your phone/device software, which will help prevent malware. Enable accounts to use multifactor authentication (MFA), which will make it harder for scammers to succeed, even if they do get some info from you. For even more protection, Yubico suggests seeking out modern phishing-resistant MFA options with hardware security keys, like their YubiKeys. And finally, trust yourself. “If your gut
The Terrifying Way A New Email Scam Is Stealing People's Money

An email hits your inbox from an unknown sender that includes a picture of your house and address, followed by a threat: “Don’t even try to hide from this. You have no idea what I’m capable of….I’ve got footage of you doing embarrassing things in your house (nice setup, by the way).” Sounds like a scene out of a horror film, right? Instead, it’s one of the latest phishing scams. Like many other email and text scams, this particular extortion scheme uses specific personal information to deceive people into sending money. The email convinces people the hacker knows more about them and that they must exchange payment or Bitcoin in order to keep their information safe. “I received a PDF over email that included my address and photo of the address and made outrageous claims about my private behavior, and claimed to have video documentation captured from spyware on my computer,” Jamie Beckland, a chief product officer at the tech company APIContext, told HuffPost. “The scammer threatened to release the video if I didn’t pay them via Bitcoin.” If you get a similar email, here are the steps you can take to figure out if it’s a scam so you protect yourself: Confirm the house and street imagery on Google Maps. Many phishing emails are often riddled with grammatical errors and poor formatting, which make them easier to identify. However, this scam, which includes images of people’s homes, is a newer, darker twist. You might be asking yourself, how exactly was the scammer able to identify your house address? According to Al Iverson, a cyber expert and industry research and community engagement lead at the software company Valimail, the sender likely found your address from a prior data breach that leaked personal data, and then used a Google Maps photo to put together an email.
Frustrierende Erfahrungen mit Kreditkartenbetrug: Ein Lehrstück aus Florida

Joel Weiss, 85 Jahre alt und Einwohner von Boca Raton, Florida, staunte nicht schlecht, als er auf seiner aktuellen Citibank-Abrechnung verdächtige Posten entdeckte – darunter eine Ausgaben von 3.000 Dollar in Indiana, DVDs von King Kong und mehrere nicht nachvollziehbare Amazon-Käufe. Da er weder etwas bei Amazon im Jahr 2024 bestellt hatte noch jemanden in Indiana kannte, vermutete er Betrug und kontaktierte umgehend seine Bank, um seine Kreditkarte sperren zu lassen. Doch auch nach zwei Monaten blieben seine Konten weiterhin aktiv und die fragwürdigen Abbuchungen mehrten sich. Sein Sohn, Matthew Weiss, der ihm in der Angelegenheit beisteht, berichtete, dass die Kommunikation mit verschiedenen Kundendienst- und Betrugsmitarbeitern von Citibank äußerst frustrierend verlaufen sei. Obwohl die Karte seines Vaters nach dem ersten Anruf eingefroren und durch eine neue ersetzt wurde, liefen weiterhin unfreiwillige Abbuchungen. Laut Yashin Manraj, CEO von Pvotal Technologies, gibt es ein System, das wiederkehrende Zahlungen trotz Kartentausch fortsetzt, um Sicht-Dienstleistungen nicht zu beeinträchtigen. Diese Lösung hat jedoch auch Tücken, wie sich zeigt. Manraj erklärte, dass Händler und Kreditkartenprozessoren Mechanismen eingeführt haben, die den Übergang zwischen alten und neuen Kartendaten erleichtern sollen. Leider kann dies auch unbeabsichtigt zu einem Fortbestehen des Betrugs führen, wenn die alte Karte gesperrt wurde und die neuen Informationen ohne Kenntnis des Nutzers übertragen werden. Alexander Hall, Architekt für Vertrauen und Sicherheit bei Sift, betonte, dass Banken möglicherweise nicht sofort das Konto schließen, um die betrügerischen Transaktionen besser nachverfolgen und anfechten zu können. Zeitgleich geriet Citibank im Januar in die Schlagzeilen, als die New Yorker Generalstaatsanwältin Letitia James die Bank verklagte, weil sie Betrugsopfer angeblich nicht ausreichend unterstützte. Experten, die von GOBankingRates befragt wurden, empfehlen einige Strategien für den Umgang mit solchen Herausforderungen bei der Kreditkartenverwaltung. Dazu gehört das Einfrieren der Kreditwürdigkeit oder das Setzen eines Fraud Alerts bei den großen Kreditbüros, um zusätzlichen Schutz zu gewährleisten. Yashin Manraj empfiehlt darüber hinaus, in besonderen Fällen das Kreditlimit auf einen symbolischen Dollar zu senken, um weiteren Missbrauch zu verhindern – auch wenn dies negative Auswirkungen auf die Bonität haben kann. Chris Borkenhagen von Authentic ID rät, im Hartnäckigkeitsfall formelle Beschwerden bei der FBI oder der CFPB einzureichen, um das Problem an die zuständigen Stellen weiterzuleiten und die Banken unter Druck zu setzen. Die Herausforderung, ein Konto nach dem Tod eines Betrugsopfers zu schließen, bleibt ebenfalls bestehen, obwohl entsprechende Richtlinien existieren, um den Prozess für Hinterbliebene zu erleichtern
5 Things To Do if Your Bank Refuses To Cancel Your Credit Card After Fraud

When 85-year-old Joel Weiss* of Boca Raton, Florida, opened his Citibank statement, he was alarmed to see recent charges he did not recognize — among them, a $3,000 retail expenditure in Indiana, King Kong DVDs, and several untraceable Amazon purchases. Not only had he not bought anything from Amazon in 2024, be he also didn’t know anyone in Indiana. Suspecting fraud, Weiss called his bank to cancel his credit card and, in effect, close his account. That was two months ago — meanwhile, his account remains open while suspicious charges accrue. “I have spoken to at least five to six customer service and fraud agents at Citi. It has been a very frustrating experience,” stated his son, Matthew Weiss,* who has been assisting his father. After his father’s initial call to Citibank, Weiss’ card was frozen and he was issued a replacement card in the mail. This made his previous card inactive, but it did not stop recurring charges to his account. “For the alleged customer’s convenience and to avoid disrupting legitimate services, [banks] allow recurring charges if the customer account is in good standing,” stated Yashin Manraj, CEO of Pvotal Technologies. Yet, not all recurring charges were his.
유럽, EV 시장판도 뒤바뀐다...미국은 커넥티드카 규제로 연 판매량 2만6000대 줄어
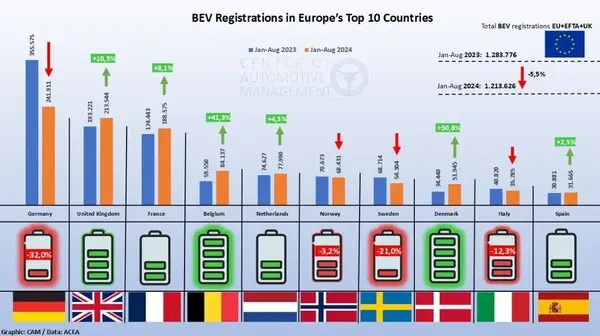
유럽의 전기차(EV) 판매가 전반적으로 줄어듦과 함께 국가별 전기차 시장의 지형이 뒤바뀌고 있다. 해외 미디어 클린테크니카는 29일(현지시각) 유럽의 전기차 판매 현황을 분석한 독일의 싱크탱크 자동차 관리 센터(CAM-Center of Automotive Management) 연구를 소개했다. CAM의 스테판 브라첼 소장은 “2023년 1월부터 8월 31일까지 유럽에서 약 128만 대의 신규 전기차가 판매됐고, 올해 같은 기간에는 121만 대로 판매량이 줄어들었다”고 말했다. 이는 전년도보다 5.5% 감소한 수치다. 브라첼 소장은 “유럽 시장에서 상당한 변화가 일어나고 있다”며 “독일에서는 EV 판매가 감소했지만, 상당한 성장을 맛본 국가들도 있었다”고 설명했다. 독일 EV판매 32% 감소...영국 10%대 성장률로 왕위 쟁탈전 독일은 유럽 최대의 신차 시장이다. 그러나, 신차 판매량이 올해 8월까지 32% 감소했다. 이는 독일이 2023년 12월에 전기차 판매에 대한 환경 보조금을 중단하면서, 만료 이전에 신차 판매량이 증가했기 때문으로 분석된다. 독일은 2023년 1월부터 8월까지 약 36만 대의 신규 전기차가 등록됐으나, 올해 같은 기간에는 24만 대에 그쳤다. 반면, 영국은 10.5%의 높은 성장세를 보였다. 올해는 21만 대의 전기차가 등록됐다. 독일의 상황이 바뀌지 않으면 영국은 유럽 최대의 전기차 시장이 될 수 있다고 브라첼 소장은 분석했다. 그는 “이 모멘텀을 기반으로 영국은 독일과의 격차를 좁히고 있고 곧 유럽 시장에서 선두를 차지할 수 있을 것”이라고 전망했다. 신규차 등록대수 기준으로 꼽은 유럽의 상위 10대 국가다. 2023년과 2024년의 등록대수를 비교했을 때 덴마크가 가장 큰 성장률을 보였다./CAM 영국뿐만 아니라, 프랑스도 신규 전기차 등록 3위 시장으로 독일을 추격하고 있다. 프랑스에서는 현재 신규 등록차량이 19만 대로 집계됐다. 4위는 벨기에로 41.3% 증가율과 8만4000대의 판매량을 기록했고 가장 높은 성장률을 기록한 국가는 덴마크였다. 5만2000대의 신규 전기차가 등록됐는데, 지난해에는 3만4000대에 불과한 수준이었다. 스웨덴은 덴마크보다 많은 5만4000대가 판매됐으나, 판매량이 지난해보다 21% 줄어들었다. 이탈리아는 12% 줄어든 3만6000대를 판매했고, 2.5% 늘어난 3만2000대 판매한 스페인이 그 뒤를 이었다. 유럽의 모든 차량 제조기업들은 EU 배기가스 규제인 유로7을 준수하기 위해 전기차 개발에 박차를 가할 것으로 예상된다. 미국의 싱크탱크 국제청정교통위원회(International Council on Clean Transportation, ICCT)의 피터 모크 회장은 해외 미디어 일렉트라이브(Electrive)와의 인터뷰에서“유럽 자동차 판매량의 25%는 전기차가 될 것”이라며 “2029년에도 해당 수치는 계속해서 유지될 것”이라고 전망했다. 커넥티드 카 규제, 업계에서 우려의 목소리 나와 미국은 연간 자동차 판매량이 감소하고, 차 값은 오를 것으로 예상된다. 미국 상무부는 27일(현지시각) 커넥티드카 금지 조처로 인해 미국 시장에서 연간 자동차 판매량이 약 2만6000대씩 줄어들 것으로 전망했다고 로이터 통신은 전했다. 커넥티드카 금지 조처는 개인 정보 보호를 이유로 커넥티드카에 중국 소프트웨어와 하드웨어를 사용하지 못하게 막는 규제다. 이는 사실상 중국산 차량 판매를 미국에서 금지하겠다는 조처다. 상무부는 해당 규정으로 인해 15억에서 23억달러(약 2조~3조원) 규모의 중국과 러시아산 자동차 수입을 제한할 수 있을 것으로 예측했다. 업계에서는 우려의 목소리도 나오고 있다. 해외미디어 더 내셔널에 따르면, 미국 기술 제조업체 피보탈 테크놀로지스(Pvotal Technologies)의 CEO 야신 만라즈는 “해당 규제로 인해 자동차 제조업체가 이에 맞는 제품을 만들거나 어떻게 수리할지에 대한 방향성이 구체적으로 나오지 않았기에 업계 전반이 어려움을 겪을 것”이라며 “가격이 일시적으로 상승하고 차량 생산이 지연될 수 있다”고 말했다. 미국의 대형차 회사들의 연합인 자동차혁신연합(Alliance for Automotive Innovation)의 CEO 존 보젤라는 "오늘날의 커넥티드 카 공급망에는 중국에서 미국으로 유입되는 기술이 거의 없지만, 이 규칙으로 인해 일부 회사는 새로운 공급업체를 찾아야 할 것”이라고 말했다. 그는 “세계에서 가장 복잡한 공급망에 대해 스위치를 켜고 끄는 것처럼 하룻밤 사이에 바꿀 수는 없다”고 지적했다.
OpenAI’s Shift to for-Profit Model Stirs Debate on AI Innovation and Competition

OpenAI, the creator of ChatGPT, is reportedly considering transitioning to a for-profit model. This strategic pivot is reshaping the artificial intelligence (AI) landscape, raising questions about the future of AI innovation, market competition and partnerships in the tech world. The potential shift comes at a crucial time when AI technology is becoming integrated into consumer products and enterprise solutions. OpenAI’s new business approach will likely have significant implications for its relationships with key stakeholders, notably Apple and Microsoft, while also affecting its standing among potential rivals. Industry experts suggest this move could lead to tighter collaborations and deeper integrations with major platforms. “Already, deep integrations exist in place, while a new spotlight by OpenAI might directly align their capabilities further with these platforms,” John Russo, VP of healthcare solutions at OSP, told PYMNTS. “That would mean tighter collaboration in the expansion of AI applications across their ecosystems.” However, this alignment may present challenges, especially with companies known for strict privacy policies. Russo points out that Apple “may want strategic changes in the model to fit their strict guidelines.” Realignment in the Industry The recent partnership between OpenAI and Apple is particularly noteworthy in light of the shift to a for-profit model. “Its partnership with Apple, particularly integrating ChatGPT into iOS 18, is a game-changer, giving OpenAI unprecedented access to the consumer market,” Kaveh Vahdat, founder and CEO of RiseAngle, a generative AI game creation company, told PYMNTS. Meanwhile, Microsoft’s substantial investment in OpenAI positions it to reap significant benefits from this partnership. Vahdat notes, “Microsoft’s deep investment in OpenAI means they stand to gain significantly from this partnership, positioning themselves as key beneficiaries of the AI boom.” Balancing Act One of the most intriguing aspects of OpenAI’s new for-profit status is its potential impact on equity ties with rivals like Google, Meta and Amazon. Russo characterizes this as “the most delicate balancing act,” saying, “On the one hand, this could provide OpenAI with special access to resources, infrastructure, or talent that could move things faster for its innovation. It also brings a very real potential for conflict of interest, especially with how deeply invested these companies are in their own AI projects.” The move to a for-profit model may also intensify regulatory scrutiny. Vahdat said, “As regulatory scrutiny ramps up, particularly with inquiries from the FTC, the balance between cooperation and competition is delicate.” However, not all experts anticipate immediate conflicts. Yashin Manraj, CEO of Pvotal Technologies, offers a different perspective on these equity ties. “Due to AI’s rapid evolution and fear of oversight or new regulations, I believe it is unlikely that Google, Meta or Amazon will create any conflict or restrictions as long as the mutually beneficial relationship continues: OpenAI is still entirely dependent on their data centers, data, and infrastructure.”