Executive Summary
In an era where cybersecurity threats loom larger than ever, the vulnerabilities arising from human access and interventions continue to be a pervasive challenge. This white paper explores the pressing issue of human-induced vulnerabilities and introduces LowOps—a revolutionary approach that leverages cloud-first features and container deployment methodology. By systematically reducing human involvement to critical “break glass” procedures, LowOps fortifies the cybersecurity posture at its core. This paper delves into key issues plaguing the current cybersecurity landscape, unveils the fundamental tenets of LowOps, and provides real-world examples of its effectiveness.
One key insight is that robot agents, in contrast to their human counterparts, can substantially enhance complexity and employ distinct runtime service accounts within various network-isolated environments. This significant shift in runtime behavior, coupled with a systematic embrace of hardened containers, considerably reduces the likelihood of tactics like lateral movement and spear phishing, which attackers often exploit to gain complete control of the environment.
Through the implementation of automation, infrastructure as code (IaC), decoupled architectures, and continuous monitoring, LowOps directly addresses the problem of inherent human factor for a robot agent model.
Introducing LowOps: A Fundamental Enhancement
The world of cybersecurity is filled with challenges, with one of the most significant being the vulnerabilities that arise from human access and manual actions. LowOps positions itself as an enhancement to an existing Zero trust position as it doesn’t define how infrastructure must be managed. These vulnerabilities can be exploited by attackers in various ways, such as direct hacking or spear phishing, leading to the exposure of crucial weak points in the system.
Often, cybersecurity solutions emphasize guarding the perimeter, but they overlook the essential aspect of human roles in the deployment process, where permissions might remain unchanged.
This neglect can lead to more services being vulnerable, thereby expanding an organization’s attackable area. Enter “LowOps,” or “Low Operations.” This approach represents a significant shift in enterprise IT. It capitalizes on the benefits of cloud-first technologies and emphasizes the methodical deployment of containers. The focus is on running them with minimal binary images and the least Linux capabilities. They operate on secure hosts, similar to Google’s container-optimized OS, and benefit from cloud-based tracing and logging. A fundamental principle is that only automated tools, like Terraform agents or Argo Workflow templated deployment, handle infrastructure changes, not manual human interventions.
The Impact of the Human Vulnerability Factor: Statistical View
| 80% of data breaches involve compromised or weak credentials. |
15% increase in social engineering attacks in the last year. |
| $5.2 million is the average cost to a business per data breach. |
25% is the average decrease in stock price, due to loss of customer trust. |
The Inefficiency of Older Methods
On average, employee cybersecurity training programs have yielded a meager 20% improvement in compliance, underscoring the ineffectiveness of the traditional human-centric monolithic deployment approach. In the last three years, automation has markedly heightened the intricacy and deployment frequency of custom resource definitions, particularly in technologies such as Kubernetes, Istio, and serverless applications. Significantly, with the implementation of these systems, the fallback option of having humans in operations manage aspects of the process, a practice prevalent in the era of monolithic deployments, is no longer viable.
Devastating Examples
| The infamous SolarWinds attack—a single compromised login led to widespread havoc, impacting thousands of organizations, including the US government. The class action lawsuit that ensued, resulted in SolarWinds paying out $26 million to shareholders. |
The recent attack on MGM and Caesars Palace exposed the brittleness of SMS-based two-factor authentication. Casino operators ended up paying $15 million as ransom to the hackers. |
LowOps: The Paradigm Shift
Defining LowOps
LowOps is a comprehensive approach to designing and operating IT systems. It goes
beyond architecture, and defines all aspects of enterprise IT infrastructure. LowOps
emphasizes:
Automation of Routine Tasks: Tasks like patching, adjusting scaling limits are automated. To focus only on more cognitive intensive tasks.
Infrastructure as Code (IaC): Provisioning and managing infrastructure through code and software development techniques.
Decoupled Architectures: Embracing event sourced microservices architectures for independent updates, scaling, and security enhancements.
Cloud native tools: Some Cloud native tools are much better than open source alternatives. Notably constant monitoring and feedback loops to refine and automate cloud operations.
Mitigating Human-Induced Vulnerabilities with LowOps
Automated Credential Management: Daily to weekly credential rotation limits the possible persistent attacker cloud access, whereas this isn’t operationally possible with human credentials. Additionally for platforms requiring administrative access, we tend to prefer openID login or direct U2F login or code based authentication to remove as possible passwords from the user flow to increase security while improving user experience.
Cascading Updates and Version Control: Infrastructure as Code (IaC) facilitates seamless updates triggered by changes in either base terraform modules from Bootstrap downwards in the different pipelines or the individual yaml configuration to behave more as infrastructure as data.
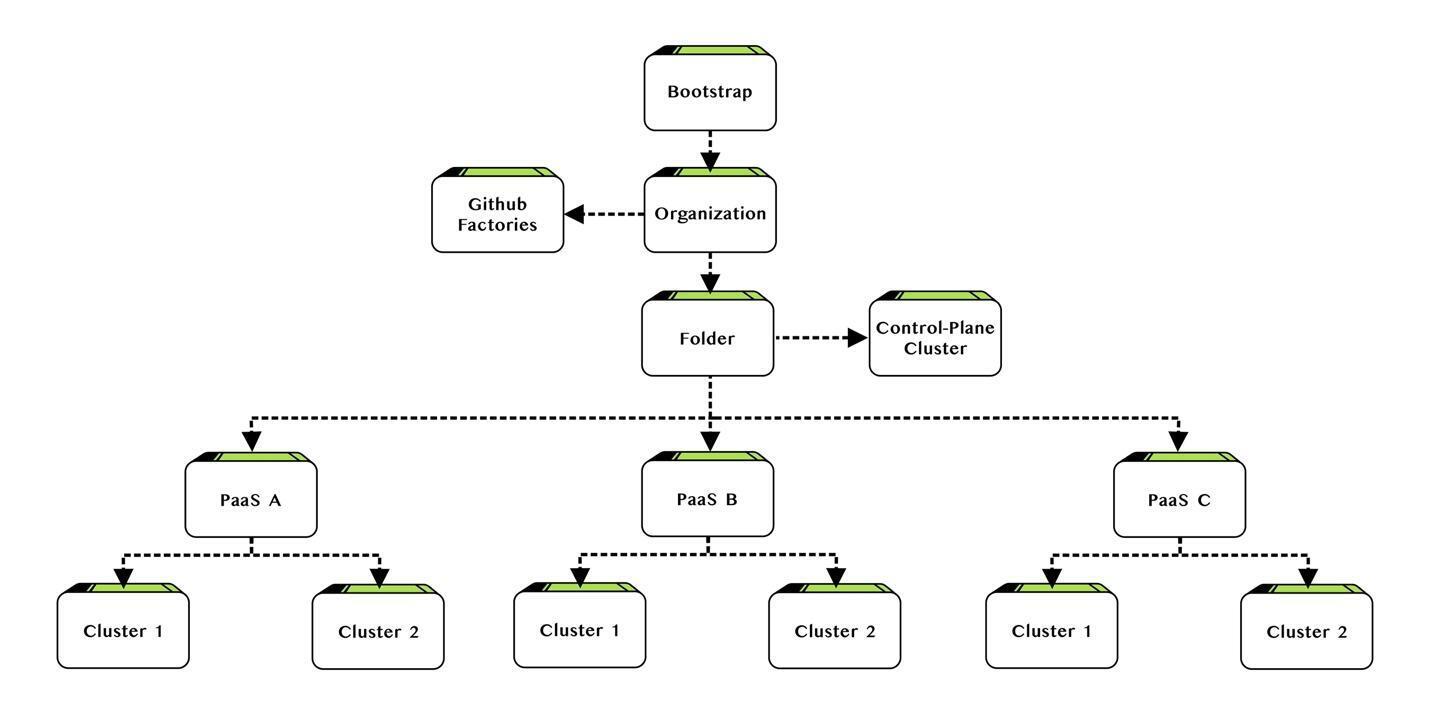
LowOps, DevOps without manual pipelines
DevOps was initially designed to ease the transfer of code between developers, operations, and testers. LowOps, however, elevates this idea. It refines the DevOps framework to be even more streamlined and automated. As a second system after the Terraform cascading structure presented earlier, we introduced a custom release engine specifically for containers. This engine comes with an embedded approval process identifying release and approval permissions per user, providing clear visibility into deployments and detailed changelogs across different environments. To execute these deployments, our engine controls multiple Argo Workflows engines.
LowOps container deployment must also stand out for its user-friendliness to non-technical people for release management. You should not have to be a seasoned DevOps professional to benefit from a LowOps platform. It must be intuitive, ready-to-use to ensure that most can utilize its features for deployment approbation and execution unless we’re adding new deployment targets or integrating new programming languages.
Unlocking the Benefits of LowOps
In its nascent stages, LowOps already presents a multitude of advantages for its users. However, the horizon promises an even richer tapestry of benefits as third-party LowOps platforms, open-source tools, and multi-cloud solutions continue to evolve.
Lower People Costs: While automation cannot entirely supplant human intelligence, it possesses the transformative power to simplify complex processes, rendering a portion of the existing workforce less indispensable. The efficiency gains brought about by automation can lead to cost savings, restructuring workforces for optimal productivity.
More Time Devoted to Development & IT Operations: In the realm of fully automated IT environments, exemplified by LowOps models, a profound shift occurs. Developers find themselves unburdened by routine tasks, enabling them to channel their energies into crafting code of superior quality. Concurrently, IT operations personnel gain invaluable time for infrastructure management and meticulous cost control, fostering a culture of innovation and efficiency.
Mitigating the Human Error Factor & Its Ramifications: While the setup of IT environments remains inherently tethered to human intervention, automation serves as a powerful ally in the battle against human errors. The potential for checkboxes to be mistakenly toggled or untoggled is omnipresent; nevertheless, automation mitigates such errors and curtails their adverse impact. This reassures organizations in their pursuit of unwavering operational excellence.
Enhanced Cloud Cost Optimization: For many cloud-based enterprises, Cloud Cost Management stands as a paramount concern, second only to security. By allowing users to pay solely for consumed capacity and diminishing—or potentially eradicating—idle time, these systems usher in a new era of cloud cost optimization
Exemplifying the LowOps Approach
The LowOps approach has been implemented in real-life scenarios and the outcomes have been very positive. Here are a couple of case examples of LowOps in action.
| CASE EXAMPLE X1 Betting Engine |
||
| Challenge | LowOps Solution | Outcome |
| To address rising cyber threats in the gambling sector with built-in infrastructure security and regular automated upgrade without downtime | To achieve gaming-compliant configurations through templated environments and real-time monitoring. | Higher throughput by a factor of least 20 by leveraging novel gRPC-web event sourcing all while upgrading all layers regularly |
| CASE EXAMPLE World Cup Event Management Solution |
||
| Challenge | LowOps Solution | Outcome |
| Synchronize client application with two custom apps one for administration another for android payment with custom inventory in a matter weeks | Leverage advanced deployment with prebuilt libraries and security to quickly up the infrastructure and deploy the applications | Added new payment methods a few days before the event on top of handling most of the cashless operations during the event |
Conclusion
The LowOps approach offers a transformative solution to the persistent issue of human-induced vulnerabilities in cybersecurity. By automating routine tasks, embracing infrastructure as code, decoupling architectures, and emphasizing continuous monitoring, LowOps provides organizations with the means to mitigate risks efficiently and effectively, all while improving technology capabilities. The case studies presented demonstrate the tangible benefits of LowOps in real-world scenarios. Embracing LowOps is the path forward to a more affordable secure digital landscape.