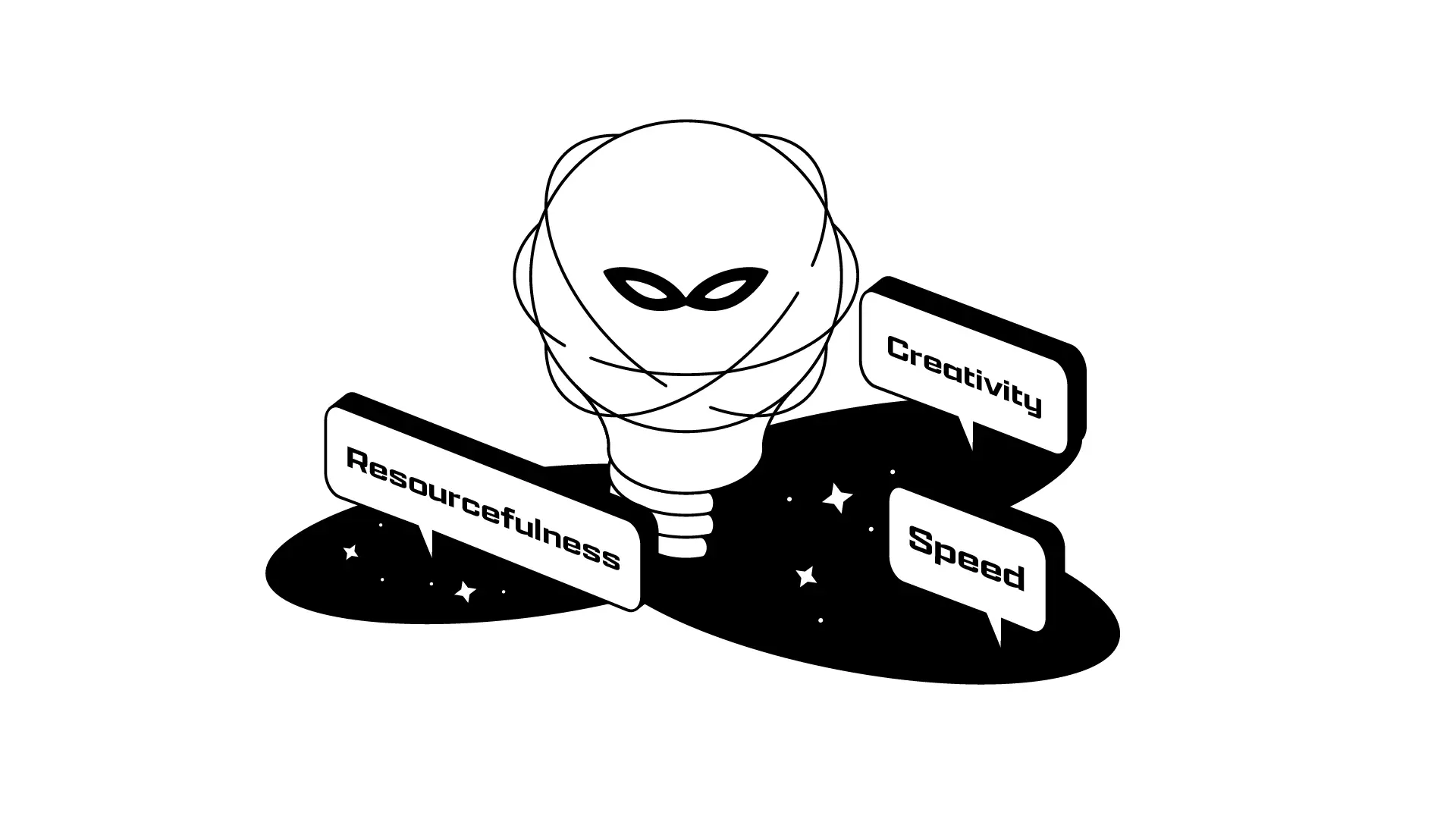
A recent article from Harvard Business Review explores the mindset of today’s cyber hackers and explains why effective cybersecurity has become so challenging by outlining the three traits shared by every successful hacker: creativity, speed, and resourcefulness. Hackers who can successfully leverage these traits are able to assault a company’s defenses with an ever-evolving barrage of novel and impactful attacks.
Thus, to remain secure, companies must be prepared for the unknown. Today’s threat landscape includes tried-and-true attacks -- phishing, social engineering, and DoS attacks -- as well as innovative strategies driven by creativity, speed, and resourcefulness. The latter are designed to exploit weaknesses before companies discover they exist. The following approaches to cybersecurity can help companies develop a future-proof framework that anticipates and addresses hidden threats.
Proactive, offensive security
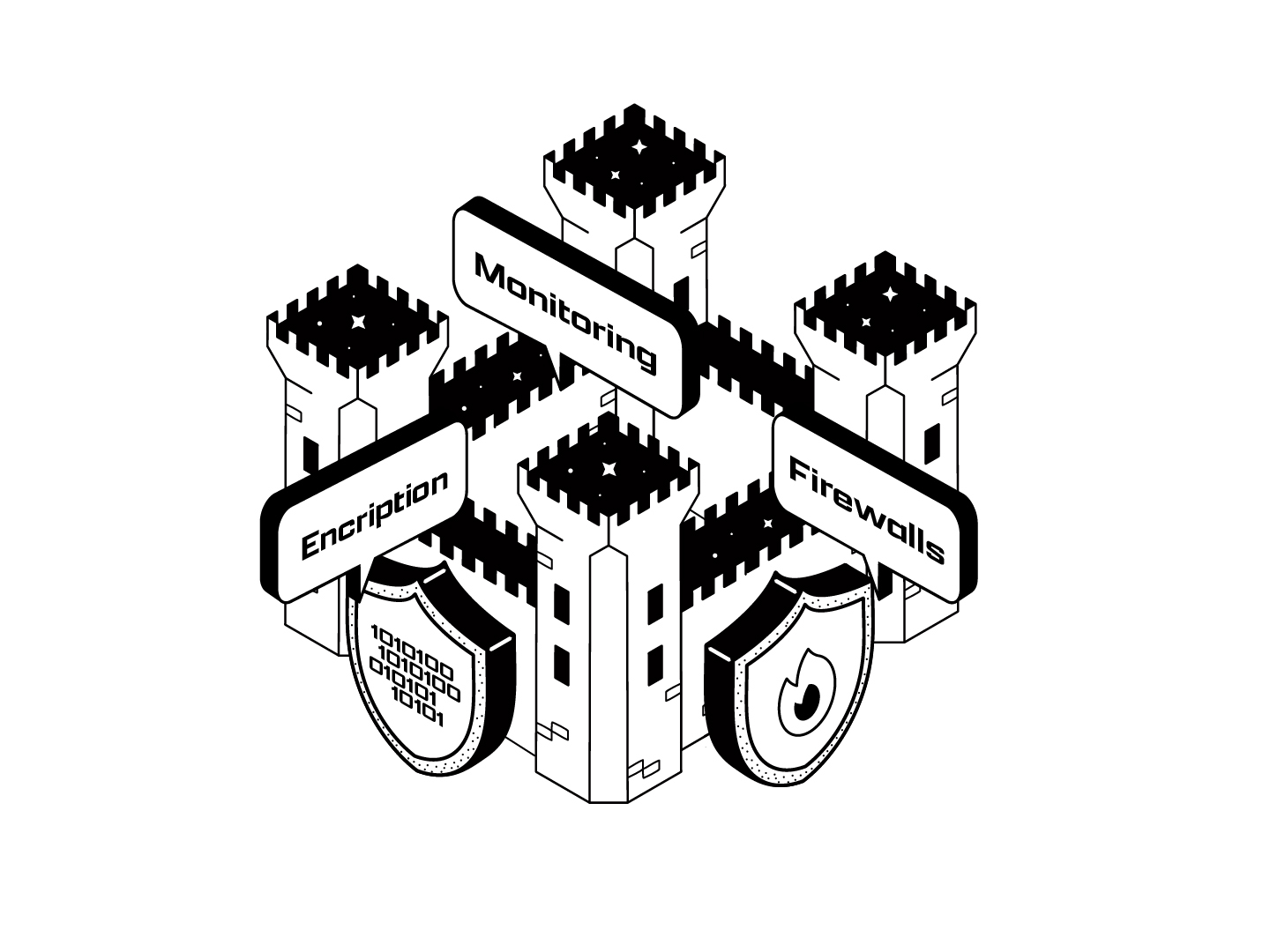
Most companies rely heavily on defensive cybersecurity to protect their data and operations. Encryption, firewalls, and network segmentation are examples of defensive security designs to repel attacks known to be employed by hackers with safeguards that address specific attack vectors.
Offensive cybersecurity seeks to emulate an attacker's actions to identify where a company’s defenses are weak. This proactive (rather than reactive) approach identifies vulnerabilities before they compromise security. Red teaming, in which simulated cyber attacks are used to test defenses, is an example of offensive security.
Proactive defensive security measures are a necessity in the modern cybersecurity landscape. However, they must still be used hand-in-hand with offensive practices to provide cybersecurity defenses that are future-proof.
Zero trust architecture
Zero trust architecture is an example of an approach that blends defensive and offensive measures. Essentially, this approach requires that credentials always be provided before access is granted. “Never trust, always verify” is the driving concept behind zero trust architecture.
Companies that employ a zero trust approach to cybersecurity can better anticipate and defend against common attack patterns, such as a hacker using easily guessed passwords to gain unauthorized access to a network. However, zero trust also leverages the “never trust, always verify” policy as a blanket response that can thwart novel approaches as they emerge.
Utilizing automations to assist with network maintenance is an approach that can enhance a company’s zero trust defenses because zero trust automations frustrate attack vectors focused on exploiting breakdowns in security team performance. By integrating processes such as security patching into a platform’s coding, companies can do away with the need to trust employees to ensure security updates are carried out in a timely and complete manner.
End-to-end infrastructure control
The more companies rely on third-party providers for cybersecurity, the more difficult it will be to develop a future-proof framework. Assessing the degree to which third-party components are kept up-to-date and reliable will always be difficult, if not impossible. Recent studies show that third-party attack vectors are now responsible for nearly 30 percent of cybersecurity breaches.
Companies that maintain end-to-end control of their infrastructure can ensure their systems grow hand-in-hand with reliable security. Each component can be assessed and tested in-house before, during, and after it is deployed. End-to-end control also allows companies to know sooner when new vulnerabilities are discovered or breaches occur, reducing the risk of widespread damage.
Every company operating in today’s business landscape must ensure its digital assets and infrastructure are protected by systems that can stand up to the creativity, speed, and resourcefulness of cyber criminals. Companies that adopt a proactive, zero trust approach that removes the risks of third-party vulnerabilities can anticipate and thwart the latest hackers have to offer.
Written by Yashin Manraj.
Yashin Manraj, CEO of Pvotal Technologies, has served as a computational chemist in academia, an engineer working on novel challenges at the nanoscale, and a thought leader building more secure systems at the world’s best engineering firms. His deep technical knowledge from product development, design, business insights, and coding provides a unique nexus to identify and solve gaps in the product pipeline. The Pvotal mission is to build sophisticated enterprises with no limits that are built for rapid change, seamless communication, top-notch security, and scalability to infinity.