How the Microsoft and CrowdStrike Failure Occurred and How to Prevent It from Happening Again

Although many consumers likely didn't know the name CrowdStrike before July 19, 2024, an incident occurred that day that caused the cybersecurity firm to become the subject of intense public scrutiny. An update to CrowdStrike's system caused many businesses running on Windows computers to crash and become entirely inoperable, affecting companies from Delta Airlines to Mr. Beast's YouTube channel.
The Biden Administration’s AI Regulation Stance

In a move that has triggered a whirlwind of responses, the Biden Administration has decided not to immediately regulate the development of AI. The revelations came in a report from the US Department of Commerce’s National Telecommunications and Information Administration. The report clearly states that “the government will not be immediately restricting the wide availability of open model weights.”
White House opts to not add regulatory restrictions on AI development – for now

The Biden Administration on Tuesday issued an AI report in which it said it would not be “immediately restricting the wide availability of open model weights [numerical parameters that help determine a model’s response to inputs] in the largest AI systems,” but it stressed that it might change that position at an unspecified point.
Could eBPF Save Us From CrowdStrike-Style Disasters?

In the aftermath of the CrowdStrike Windows security fiasco, security experts and developers alike are looking for a safer way to run low-level security programs. In a recent blog post, Brendan Gregg, a well-regarded system performance expert and Intel Fellow, suggests we can keep computers from crashing due to bad software updates, even those updates that involve kernel code,” thanks to eBPF.
Microsoft Patent Tracks Down Software Vulnerabilities, Cyberattacks
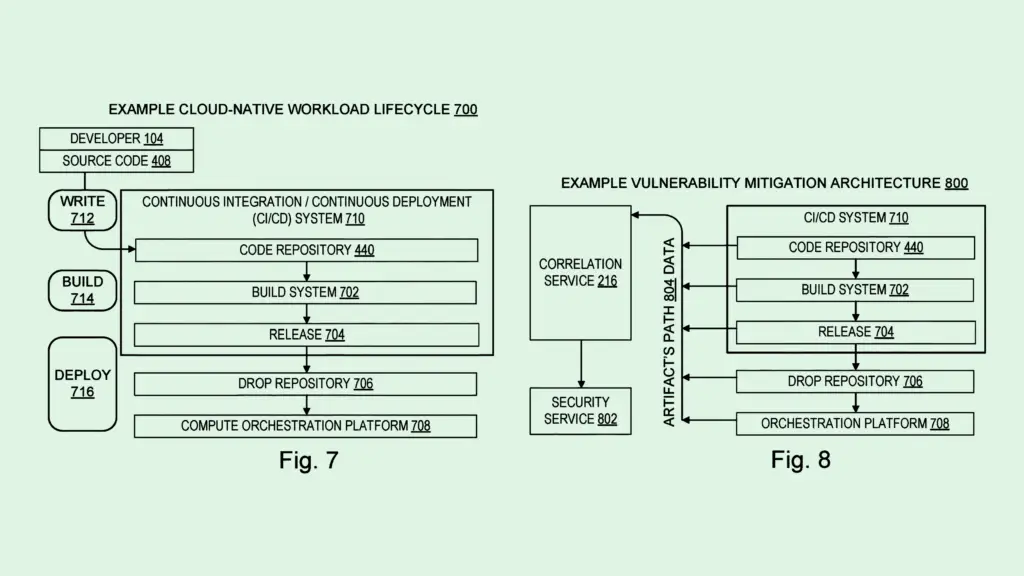
The tech firm is seeking to patent “security vulnerability lifecycle scope identification,” aiming to find faults in source code through different stages of development and deployment. The goal is to identify “the scope of performance flaws and security vulnerabilities” and avoid trying solutions that are “unnecessarily inefficient or incomplete.”
Building the Infinite Enterprise with Pvotal Technologies

Business is entering the age of the infinite enterprise. To thrive in this new age, companies must adopt customer-centric strategies that infinitely expand access to their goods and services and deliver an exceptional user experience across a wide variety of platforms to customers around the world, scaling with ease as new demands arise.
Cyberdefense Radio Interview II - Ashley Manraj

Ashley sits down again with Gary Miliefsky of Cyberdefense Radio. He is founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program.
Cybercriminals capitalize on CrowdStrike outage

Polyfills are pieces of programming code that provide developers with an efficient fix for a common problem and ensure that even users with outdated browsers can have the most up-to-date functionality. The usefulness of polyfills and their easy accessibility has led to their use on hundreds of thousands of sites.
Risk Lessons From CrowdStrike’s Blunder

Computer systems across the globe were still recovering this week from a massive meltdown Friday morning that spread rapidly, affecting hospitals, airlines, banks, emergency services and other organizations. Unlike other major outages over the past couple of decades, Friday’s chaos didn’t generate from an outside cyber attack. Rather, the call came from inside the house: a faulty Windows software update pushed by cybersecurity provider CrowdStrike.
Cybercriminals capitalize on CrowdStrike outage

Organized cybercriminal gangs have lost little time in attempting to cash in on the ongoing CrowdStrike/Windows outage currently affecting banks, airlines and businesses. According to the UK’s National Security Cyber Centre: “An increase in phishing referencing this outage has already been observed, as opportunistic malicious actors seek to take advantage of the situation. This may be aimed at both organizations and individuals.”